Cybersecurity refers to the technologies, processes, and practices designed to protect an organization’s intellectual property, customer data, and other sensitive information from unauthorized access by cybercriminals. The frequency and severity of cybercrime are on the rise and there is a significant need for improved cybersecurity risk management as part of every organization’s enterprise risk profile.
Regardless of your organization’s risk appetite, you need to include cybersecurity planning as part of your enterprise risk management process and ordinary business operations. It’s one of the top risks to any business.
Different Cybersecurity Risks and their preventions:
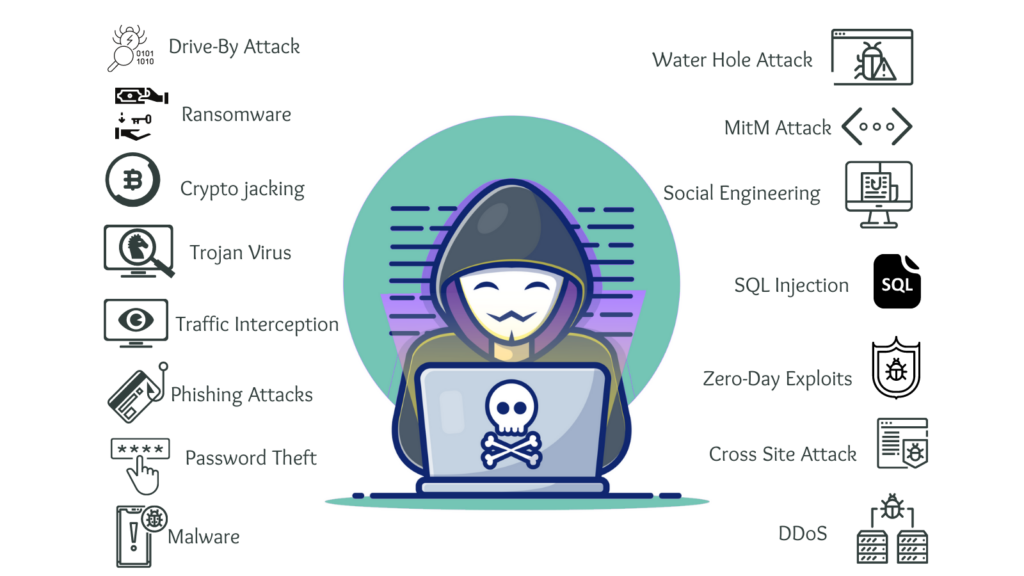
1 – Malware
We will start with the most prolific and common form of security threat: malware. It has been around since the internet’s inception and continues to remain a consistent problem. Malware is when an unwanted piece of programming or software installs itself on a target system, causing unusual behavior. This ranges from denying access to programs, deleting files, stealing information, and spreading itself to other systems.
Prevention: A proactive approach is the best defense. Common sense dictates users and organizations should have the latest anti-malware programs installed, for starters. It is also important to recognize suspicious links, files, or websites, which are effective ways of implementing malware. Often, a combination of caution and anti-virus is enough to thwart most malware concerns.
2 – Password Theft
“I’ve been hacked!” A common conclusion when you log in to an account, only to find your password changed and your details are lost. The reality is an unwanted third party managed to steal or guess your password and has since run amok with the information. It is far worse for an enterprise, which may lose sensitive data.
Prevention: There are several reasons for losing a password. Attackers may guess the password or use “brute force” programs to cycle through thousands of potential attempts. They may also steal it from an unsafe location or use social engineering to trick a user into giving it away. Two-factor authentication is a robust protection method, as it requires an additional device to complete the login. Additionally, using complicated logins thwarts brute force attempts.
3 – Traffic Interception
Also known as “eavesdropping,” traffic interception occurs when a third-party “listen” to info sent between a user and host. The kind of information stolen varies based on traffic but is often used to take logins or valuable data.
Prevention: Avoiding compromised websites (such as those not using HTML5) is an excellent proactive defense. Encrypting network traffic – such as through a VPN – is another preventive method.
4 – Phishing Attacks
Phishing scams are an older attack method and rely on social engineering to achieve their goal. Typically, an end-user receives a message or email which requests sensitive data, such as a password. Sometimes, the phishing message appears official, using legitimate appearing addresses and media. This compels an individual to click on links and accidentally give away sensitive information.
Prevention: Generally, a common-sense approach to security is the best prevention. Phishing messages are often rife with spelling and syntax errors. Official emails from organizations do not request personal data, so this is a giveaway there is malicious intent.
5 – DDoS
Distributed Denial of Service is an attack method in which malicious parties target servers and overload them with user traffic. When a server cannot handle incoming requests, the website it hosts shuts down or slows to unusable performance.
Prevention: Stopping a DDoS requires identifying malicious traffic and halting access. This can take time depending on how many malicious IPs are used to distribute the attack. In most cases, servers need to be taken offline for maintenance.
6 – Cross-Site Attack
Referred to as an XSS attack. In this instance, a third party will target a vulnerable website, typically one lacking encryption. Once targeted the dangerous code loads onto the site. When a regular user accesses said website, that payload is delivered either to their system or browser, causing the unwanted behavior. The goal is to either disrupt standard services or steal user information.
Prevention: Encryption is usually required on the host’s side. Additionally, providing the option to turn off page scripts is vital to thwart a malicious payload from activating. Users can also install script-blocker add-ons to their browser if they prefer additional browsing control.
7 – Zero-Day Exploits
Occurring after the discovery of a “zero-day vulnerability,” an exploit is a targeted attack against a system, network, or software. This attack takes advantage of an overlooked security problem, looking to cause unusual behavior, damage data, and steal information.
Prevention: Stopping exploits is challenging, as it relies on the vendor both discovering the loophole and releasing a fix for it. In some cases, a zero-day vulnerability can exist for an extended period before its discovered. Users must maintain good safety habits until a fix is released.
8 – SQL Injection
An SQL attack is essentially data manipulation, implemented to access information that is not meant to be available. Essentially, malicious third parties manipulate SQL “queries” (the typical string of code request sent to a service or server) to retrieve sensitive info.
Prevention: Implementation of smart firewalls is one prevention method; application firewalls can detect and filter out unwanted requests. Generally, the most effective way is to develop code that identifies illegal user inputs.
9 – Social Engineering
Similar to phishing, social engineering is the umbrella method for attempting to deceive users into giving away sensitive details. This can occur on any platform, and malicious parties will often go to great lengths to accomplish their goals, such as utilizing social media info.
Prevention: Remaining skeptical of suspicious messages, friend requests, emails, or attempts to collect user info from unknown third parties.
10 – MitM Attack
A Man-in-the-Middle attack occurs when a third party hijacks a session between client and host. The hacker generally cloaks itself with a spoofed IP address, disconnects the client, and requests information from the client. For example, attempting to log in to a bank session would allow a MITM attack to hijack user info related to their bank account.
Prevention: Encryption and use of HTML5 are recommended.
11 – Ransomware
A nasty variant of malware, ransomware installs itself on a user system or network. Once installed, it prevents access to functionalities (in part or whole) until a “ransom” is paid to third parties.
Prevention: Removal is challenging once installed. Keeping anti-virus updates and avoiding malicious links are the best current prevention methods. Also, current backups and replications are key to keeping ransomware attacks from becoming catastrophic.
12 – Crypto-jacking
Crypto-jacking is an attempt to install malware that forces the infected system to perform “crypto-mining,” a popular form of gaining crypto-currency. This, like other viruses, can infect unprotected systems. It is deployed because the act of crypto mining is hardware intensive.
Prevention: Keep all security apps/software updated and make sure firmware on smart devices is also using the latest version. Crypto-jacking can infect most unprotected systems.
13 – Water Hole Attack
Generally used to target organizations, water hole attacks occur when a group infects websites a particular organization frequently uses. The goal – much like a cross-site attack – is to load a malicious payload from the infected sites.
Prevention: Anti-virus can passively identify dangerous scripts. Keep website scripts off as a default if your enterprise suspects an infection.
14 – Drive-By Attack
In a drive-by-attack, malicious code is delivered onto a system or device. The distinction, however, is that no action is needed on the user end, where typically they need to click a link or download an executable.
Prevention: Avoid suspicious websites. Normally, compromised websites are flagged by search engines and anti-malware programs.
15 – Trojan Virus
Trojan malware attempts to deliver its payload by disguising itself as legitimate software. One technique used was an “alert” a user’s system was compromised by malware, recommending a scan, whereby the scan actually delivered the malware.
Prevention: Avoid downloading programs or executables from unrecognized vendors or those that attempt to alarm the user to a serious problem.
Effective Cybersecurity Risk Management
1. Build a company culture
The first thing to consider when you are planning your organization’s cybersecurity risk management program is your company’s culture. The average cost of a cyberattack now exceeds $1.1 million, and further, 37% of companies attacked see a diminution of their reputation following the attack. This is why you need to establish a cybersecurity-focused culture throughout the entire organization, from the part-time staff up to the executive suite.
2. Distribute responsibility
The burden for maintaining cybersecurity cannot rest exclusively on the IT or security departments. Every employee in the organization needs to be aware of potential risks and be responsible for preventing security breaches. Your security plans must take into account not just your hardware and software, but also human factors. According to Verizon’s 2018 Data Breach Investigations Report, 93% of all data breaches are caused by phishing.
To guard against these human-related intrusions, employees need the right tools and training to recognize malware, phishing emails, and other social engineering attacks. This is part and parcel of developing an organizational culture of security.
3. Train employees
To implement your cybersecurity plan, you need to fully train staff at all levels on the identified risks and on the procedures and systems designed to mitigate those risks. Employee training is necessary to spread and encourage a security-aware culture as well as to ensure all employees know how to use the cybersecurity systems and tools you plan to implement.
4. Share information
Putting cybersecurity in a silo will result in failure. Information about cybersecurity risks must be shared across all departments and at all levels. What you’re doing related to cybersecurity must be communicated to all the appropriate stakeholders, especially those involved in your company’s decision-making. You need to make it clear to all appropriate parties the potential business impact of relevant cyber risks—and then keep them aware and involved in ongoing activities.
5. Implement a cybersecurity framework
It is important to implement the appropriate cybersecurity framework for your company. This is typically dictated by the standards adopted by your industry. In this regard, the most frequently adopted cybersecurity frameworks are:
- PCI DSS
- ISO 27001/27002
- CIS Critical Security Controls
- NIST Framework for Improving Critical Infrastructure Security
6. Prioritize cybersecurity risks
Remember, you do not have an infinite number of employees or an unlimited budget. Put simply, you cannot protect against all possible cyber risks. Consequently, you need to prioritize risks in terms of both probability and the level of impact, and then prioritize your security preparations accordingly.
7. Encourage diverse views
Too often cybersecurity staff and management view risk from a single viewpoint, often based on personal experience or company history. But cybercriminals seldom share this same viewpoint; malicious actors are more likely to think “outside the box” and identify weak points in your system that you haven’t seen before or even considered. For this reason, it’s useful to encourage team members to think of and argue different points of view. This sort of diversity in thinking will help you identify more risks and more possible solutions.
8. Emphasize speed
When a security breach or cyberattack occurs, an immediate response is required. The longer it takes to address the threat, the more damage may be done. Studies show that 56% of IT managers take more than 60 minutes to get information about an ongoing cyberattack. But a lot of damage can be done in an hour.
The speedy reaction must be a part of your security-forward culture. That means you need to develop an early recognition of the potential risks, immediate identification of the attacks and breaches, and rapid response to security incidents. When it comes to risk containment, speed is of the essence.
9. Develop a risk assessment process
Risk assessment is an important part of any cybersecurity risk management plan. You need to:
- Identify all your company’s digital assets, including all stored data and intellectual property.
- Identify all potential cyber threats, both external (hacking, attacks, ransomware, etc.) and internal (accidental file deletion, data theft, malicious current or former employees, etc.)
- Identify the impact (financial and otherwise) if any of your assets were to be stolen or damaged.
- Rank the likelihood of each potential risk occurring.
10. Incident response plan
Finally, you need to develop an incident response plan, focusing on the priority of risks you’ve previously identified. You need to know what you need to do when a threat is detected—and who needs to do it. This plan should be codified so that even if an incident occurs after you have personally left the company, the team currently in place will have a roadmap for how to respond.
To Summarize, cybersecurity risk management is a long process, and it is an ongoing one. Your organization can never be too secure. Cyber-attacks can come from stem from any level of your organization, so it is important to not pass it off to IT and forget about it. In order to mitigate cyber risk, you need the help of every department and every employee.
If you fail to take the right precautions, your company and more importantly your customer’s data could be a risk. You need to be able to control third-party vendor risk and monitor your business for potential data breaches and leaked credentials continuously.
We at Varuna Marine can help!
Our fully managed cybersecurity solution comes with an owner dashboard that tracks all cybersecurity-related KPIs and always ensures compliance. Our team of cybersecurity experts conducts a soft and hard audit annually and every six months to ensure a complete test of readiness against external cyber-attacks.



