US NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY (NIST)
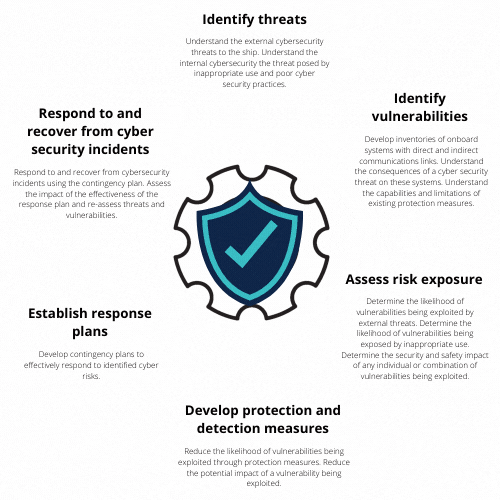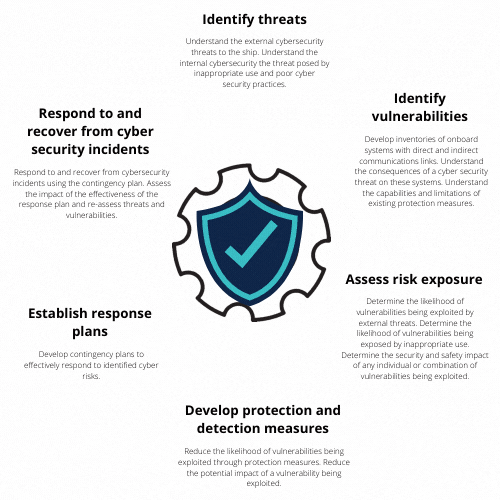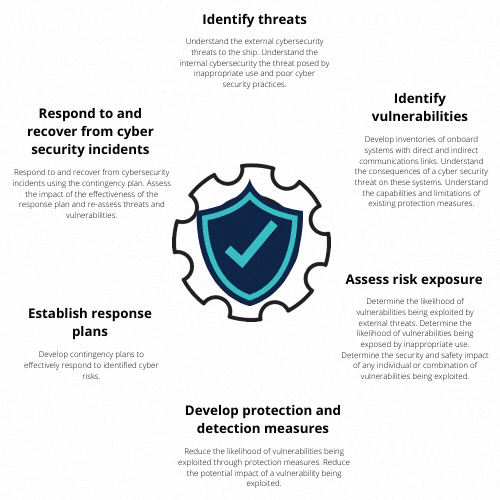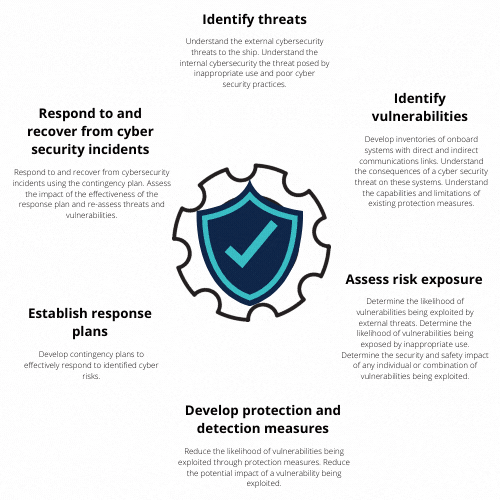
In addition to the IMO resolution, the U.S. National Institute of Standards and Technology (NIST) Cybersecurity Framework Version 1.1 is also used as a reference. The NIST Cybersecurity Framework assists companies with their approach to risk assessments by helping them understand an effective approach to manage potential cyber risks both internally and externally.
As a result of applying the Framework, a “profile” is developed, which can help to identify and prioritize actions for reducing cyber risks. The profile can also be used as a tool for aligning policy, business, and technology decisions to manage the risks.
The NIST recently released a preliminary draft of its Cybersecurity Framework Profile for Ransomware Risk Management.
INTERNATIONAL ASSOCIATION OF CLASSIFICATION SOCIETIES (IACS)
Recommendation on Cyber Resilience (No. 166) from IACS consolidates previous 12 recommendations related to cyber resilience and applies to the use of computer-based systems, which provide control, alarm, monitoring, safety or internal communication functions that are subject to the requirements of a classification society.
- In 2022, IACS published two new sets of Unified Requirements (UR) on cyber issues and the updated Rec. 166 on 27 Apr 2022. The aim of this UR is to provide a minimum set of requirements for cyber resilience of ships, with the purpose of providing technical means to stakeholders which would lead to cyber resilient ships.
- This UR targets the ship as a collective entity for cyber resilience and is intended as a base for the complementary application of other URs and industry standards addressing cyber resilience of onboard systems, equipment and components. Minimum requirements for cyber resilience of on-board systems and equipment are given in IACS UR E27.
- As long as on-board systems and equipment are part of a computer-based systems in the scope of applicability of this UR and are not considered as individual entities, for such systems and equipment more stringent requirements than those enforced in IACS UR E27 may be required as per IACS UR E27 additional system requirements to support the fulfilment of this UR.
- UR E26 aims to ensure the secure integration of both Operational Technology (OT) and Information Technology (IT) equipment into the vessel’s network during the design, construction, commissioning, and operational life of the ship. This UR targets the ship as a collective entity for cyber resilience and covers five key aspects: equipment identification, protection, attack detection, response, and recovery.
- UR E27 aims to ensure system integrity is secured and hardened by third-party equipment suppliers. This UR provides requirements for cyber resilience of onboard systems and equipment and provides additional requirements relating to the interface between users and computer-based systems onboard, as well as product design and development requirements for new devices before their implementation onboard ships.
- These URs will be applied to new ships contracted for construction on and after 1 January 2024 although the information contained therein may be applied in the interim as non-mandatory guidance.